4th Brand Protection Congress Keynote
I was honoured to be invited to speak at the 4th Brand Protection Congress in Frankfurt, Germany, 3rd & 4th December 2019, especially after attending the 2nd edition of the event last December, also held in Frankfurt, which was thoroughly insightful and well organised. Thanks to World BI for hosting the event.

I decided to speak on the subject: ‘Intermediary Liability & Future Challenges to Effective Brand Protection’ but approach the matter from a different perspective, one which is frequently overlooked at brand protection and intellectual property events. Unfortunately, it is too easy for us practitioners and attendees to industry events to suffer from diminishing horizons; we can sometimes fall into the trap of losing context and perspective. Applying a ‘criminology lens’ to brand protection issues contrasted with the some of the industry literature discussing the connections between counterfeiting and piracy with crime, in particular, news articles and opinion pieces from industry experts. In an era of heightened awareness of fake news across social media, I realised that fake news is portrayed in an overly simplistic manner, by reference to blogs, Facebook posts or tweets making absurd claims or conspiracists on Reddit or YouTube. However, fake news is not always fake. Not as such. Facts are distorted to fit a specific purpose.
Giving an ‘angle’ to a news story is as old as journalism itself. On this basis, I highly encourage you to read the source materials I relied for this presentation, mostly, they are produced by various international organisations, including the OECD, EUROPOL and the EUIPO. A link to all the references/reports cited within my slides can be found at the bottom of this page – again, please take time to read these and come to your own conclusions. Another consequence of fake news has been the rise of third-party ‘fact-checkers’, which is also open to abuse, take the UK Elections for example. All good third-party fact-checkers always urge individuals to take time to understand how to spot misleading information, rather than proclaiming themselves as emperor of fact. In the hyper-fast digital age, the rise of influencers has illuminated how willing we are to accept information without question. Rather than the democratisation of knowledge we was promised, we have created a race to the bottom for sensationalism. Hyperbole trumps reason. Understanding has been replaced by ‘likes’ and ‘retweets’.
And who is to blame? The traditional media blames social media; politicians blame social media; international organisations, law enforcement, companies, bloggers, influencers and individuals blame the platforms too. Therefore, it must be the social media platforms – so goes the logic. Politicians sit in parliaments debating the troubles social media causes modern society whilst funding exploitative social media marketing campaigns. The same applies to the traditional media companies and users of the platforms. We, ourselves, are to blame: every time we retweet fake news; accept the word of an influencer without question; shift blame from criminals to end-users or tech companies; or allow politicians to use fear tactics to speak to our deepest vulnerabilities. We have crafted incredible online communities, the responsibility is on us to safeguard these spaces, but more importantly, to safeguard the people behind the handles.
Intermediary Liability & Future Challenges to Effective Brand Protection +

Below is my keynote which I delivered on the day – I have edited and woven together other thoughts on the subject matter which I did not get time to cover whilst presenting to provide greater context. Text directly from the transcript is signalled by quotation marks. The slide deck can be downloaded for free, and hassle-free, no need to include an email address or create an account. Unfortunately, one slide has been redacted for publication of the slides.
Ineffective Brand Protection

“My name is Steven – I’m going to present Intermediary Liability & Future Challenges to Effective Brand Protection. Let’s start off with effective brand protection part, sometimes the easiest way to understand something is to look at the reverse. As such, we are going to start with ‘ineffective brand protection’, and I think anyone who has worked in anti-counterfeiting, anti-piracy, any sort of illicit trade area, law enforcement, regulatory compliance will understand what I mean when I say ‘whack-a-mole’. It is the ineffective approach when you are going after every single infringer. You can see the robot, he is confused, he has stuff coming at him left and right, he doesn’t know which way to go. He hits something, he thinks its resolved, but the issue pops right back up. This metaphor could be used to describe the endless notice and takedown approach online. That is the ineffective approach, what we don’t want. Let’s look at an effective approach.”
A target to be “number one on the Google Transparency report” in terms of URLs reported is a clear sign that the reporting organisation is more concerned with their own commercial interests above those of the rightsholders and content creators.
Notice and takedown policies are vital for rightsholders, and to dissuade and remove other forms of abusive content. The whack-a-mole point refers to strategies which are solely based around NTD or bulk de-indexing – which are not actually ‘strategies’ as such. A target to be “number one on the Google Transparency report” in terms of URLs reported is a clear sign that the reporting organisation is more concerned with their own commercial interests above those of the rightsholders and content creators.
Effective Brand Protection

“Over the last day and a half we heard a lot about what is effective. This excerpt is from the InfoSoc Directive – which was mentioned just before in regards to injunctions.”
The excerpt is specifically from rectal (59). Reading the recitals is extremely useful in understanding the context of the Directive, the rationale behind the legal jargon which follows. The context is often lost when the Directive is transposed into national law.
“The important part here is ‘In many cases such intermediaries are best placed to bring such infringing activities to an end.’ The targeting is not whether the intermediary is in the wrong, the important thing is the intermediary can provide an efficient remedy against abuse. Otherwise you are left with the whack-a-mole game, this is cost prohibitive for even the largest rightsholders. We have had a couple of good examples today [redacted], another being the tracing back of infringements to four factories. I bet it was a whole lot easier to litigate against the four factories than attempting to sue every single infringer along the supply chain. The point being, effectiveness is about targeting ‘pinch-points’ in the supply-chain. This is what we will be looking into in terms of future challenges.”
Not only is it easier and cost-effective for the rightsholder to target four large factories of counterfeiters rather than each individual, it is also a more proportionate approach to target the commercial-scale infringer.
Future Challenges

“The future challenges are coming from three different areas. These are really broad categories and there are different ways to categorise. The first I’m going to say is ‘policy’: which covers the legal framework, harmonisation of laws, trade deals, trade wars; but it also covers platforms and intermediaries and their own policies. Google, Amazon, Facebook, these huge platforms which impact the digital economy; it’s the policies they choose to implement. Content ID, for example, is YouTube’s own policy-based system introduced to provide a level of efficacy to rightsholders in removing infringing content. We hear Facebook saying the future is more encrypted/privacy-focused – I’m not sure how many people actually believe they are genuine in Facebook saying they want to protect the privacy of users. But they are definitely moving more to a WhatsApp model for all of their products, Instagram and Facebook, having encryption built-in. Those are the types of considerations in the policy category.”
“Technical: [redacted] As we can see, the technical challenges cross-over with policy, none of the areas can be considered in isolation. The implementation of GDPR had the unintended consequence of restricting access to previous Whois information so vital for cyber-investigator. All three areas obviously cross-over. The one that we are going to focus on for the rest of our time is criminality.”
Intellectual property infringement can lead to criminal sanctions, in the UK this covers trade marks, copyright and registered design rights for example.
Future Challenges: Criminality

“This excerpt is taken from the IP Crime Threat Assessment by the EUROPOL and EUIPO produced report. The interesting part is here is ‘Most criminal activity involving counterfeiting is undoubtedly performed by organised crime groups and there appears to be an overall professionalisation of these groups.’ Two key things there are: organised crime groups and professionalisation. In terms of professionalisation, I have definitely seen that from my own experience, and others sharing their experiences during this event. However, we are going to look at this in terms of how counterfeiting is often linked with terrorism and how some of the data doesn’t really reflect what is being reported. But first, let’s go on to organised crime groups.”
Know Your Criminal: OCGs
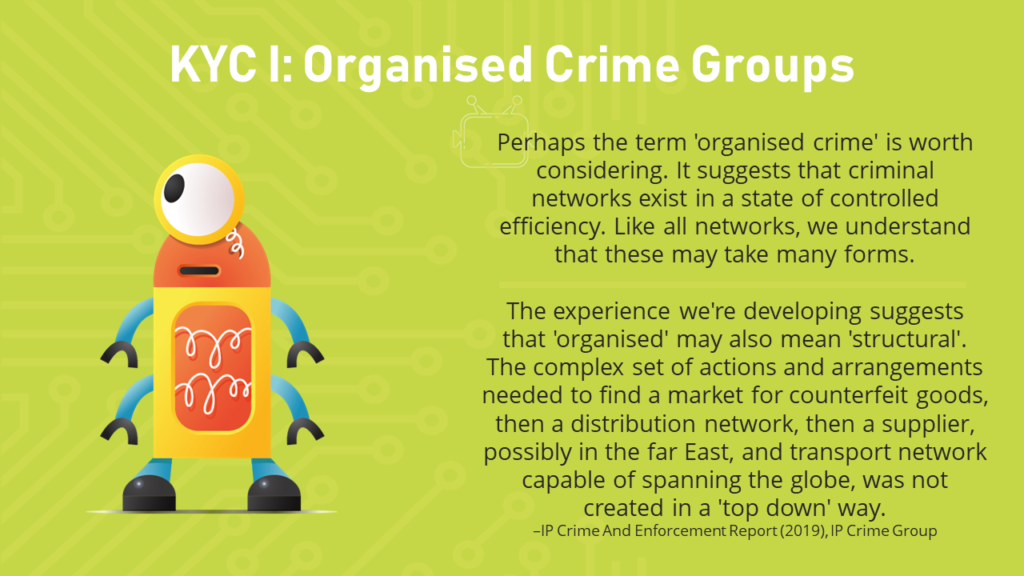
“Yesterday we heard about the KYC movement, meaning Know Your Client. Today we are going to call it Know Your Criminal. This is about OCGs, with this excerpt taken from the 2019 IP Crime and Enforcement Report produced by the IP Crime Group. They are a UK-based body made up of trade associations, rightsholders, law enforcement, trading standards, some preferential service providers, they produce yearly reports on the state of IP crime in the UK. The first line sets us up ‘Perhaps the term organised crime’ is worth considering.’ – this is exactly what we are going to do here right now. The second paragraph talks about how organised may also mean structured. Most people hear the term ‘organised crime’ or organised crime groups’ and think of the Mafia. Now these terms are being applied to online piracy and counterfeiting with a new definition for the digital economy. This is needed. Although, I think this specific definition may not be the best approach.”
“Where it says ‘a market for counterfeit goods’, if I was a counterfeiter I would call a market for counterfeits Amazon or Facebook, anywhere with reach and customers; ‘then a supplier’ this could be another ecommerce platform I will buy the items from to sell onwards on Amazon with a mark-up due to customer trust in Amazon; ‘possibly in the far East’ which could be AliExpress, an Alibaba Group company; ‘and a transport network capable of spanning the globe’ this could be ePacket delivery option which extends from China to the EU and US, its fast and cheap. This definition captures a single person who purchases a counterfeit from AliExpress to sell on Amazon as organised crime. I think dilutes the terms and takes away from our argument when we draw connections between counterfeiting and illicit trade in a more holistic manner. A broader discussion on how we should define organised crime and organised crime groups is needed within our industry.”
Diluting the definition serves only to further exacerbate the whack-a-mole approach, with critical police resources being funnelled into the lowest level of the chain and not targeted at the intersection with other forms of illicit trade.
Both Amazon and Facebook are platforms on which counterfeiters exploit to sell infringing items. Both have strong IP policies, takedown mechanisms and work alongside rightsholders to help reduce IP infringement. There are ecommerce platforms, just as there are physical markets, which are dedicated to selling counterfeit items. However, these generally gain less traffic and lower margins, therefore most counterfeiting activity online occurs on legitimate platforms.
A presentation delivered the previous day from TRACIT spoke about how counterfeiting fits into the broader discussion of illicit trade in a more holistic approach. Also, a study showed that counterfeiting directly negatively impacted nine of UN’s Sustainable Development Goals. Such framing captures the nature of illicit trade and global counterfeiting far better than drawing comparisons to individual infringers and organised crime. Diluting the definition serves only to further exacerbate the whack-a-mole approach, with critical police resources being funnelled into the lowest level of the chain and not targeted at the intersection with other forms of illicit trade. The purpose of the new definition is well-intended and needed, however, a more nuanced understanding of online culture and brand protection is needed.
Know Your Criminal: Terrorism
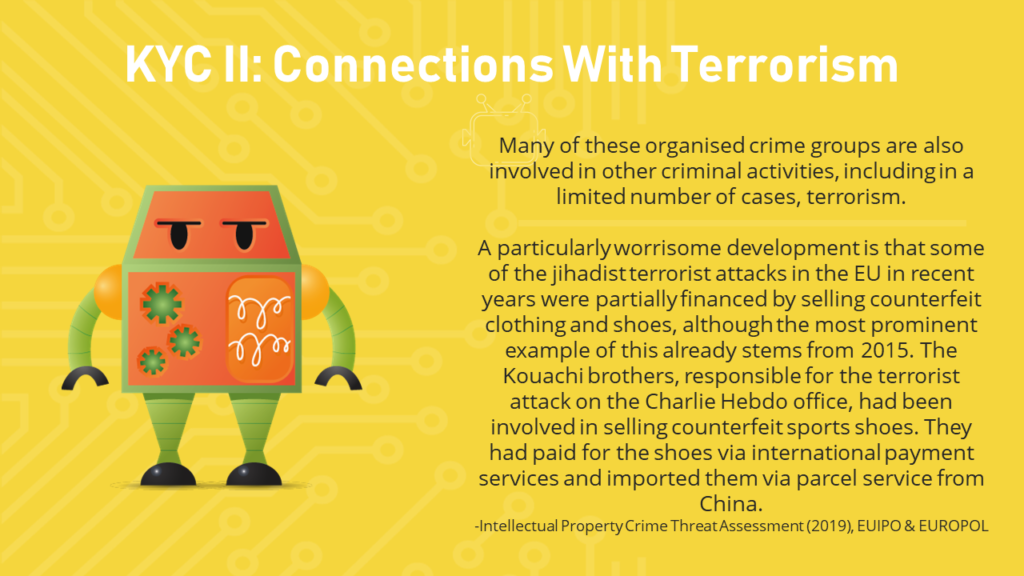
“Our second part of Know Your Criminal is the connection with terrorism. This excerpt is again taken from the EURPOL IP Crime Threat Assessment. It states ‘Many of these organised crime groups are also involved in other criminal activities, including in a limited number of cases, terrorism.’ and then the second part of the excerpt references a case which gained a lot of media attention – the Charlie Hebdo attack in 2015. It is linking the [prior] counterfeiting activities of the two perpetrators of the terrorist attack to the attack itself where it says they ‘had been involved in selling counterfeit sports shoes.’ The brothers who conducted the attack were selling counterfeit Nike.”
“This was supposedly how the brothers were making a living before conducting the terrorist attack; they were also involved in drug dealing which was stated to be their primary income. There were a few different areas of criminality the Charlie Hebdo perpetrators were involved in.”

“If we look into this in more detail, the information was taken largely from a UNIFAB report ‘Counterfeiting & Terrorism’, originally in French (Contrefaçon & Terrorisme). Fortunately for non-French readers like me it was also translated into English. The report was disappointed counterfeiting had been labelled a ‘petty crime’ by French police. Where the excerpt says petty crime, that can be read as ‘counterfeiting’. Towards the end of the excerpt it states ‘Just seven months later, the Kouachi brothers burst into the Newsroom of Charlie Hebdo’ this then becomes the link between the counterfeiting activities with the terrorist attack.”
Know Your Content: Sensationalism

“This generated a lot of media attention at the time [2016] and after the EUROPOL report was released [2019]. The IP press picked it up, for a number of reasons, here’s one example of such. It starts off ‘Why are counterfeit goods used to fund terrorism’, with the reason being prison sentences are not long enough in France and the UK. The third paragraph is a completely irrelevant example. Then ‘How do we stop counterfeit goods funding terrorism’ which talks about ‘smarter technologies capable of outsmarting terrorist and organised criminal groups’ and the need for ‘Artificial intelligence, machine learning’ etc, basically a sales pitch.”
Having brand owners and brand protection vendors repackaged as global anti-terrorism organisations stretches credibility beyond plausibility.
Also, the sales pitch mentions that it is ‘brands’ who need this smarter technology. Any rational evidence linking counterfeiting or an infringer to terrorism should be reported to the appropriate law enforcement agency – rather than contracting a brand protection service provider. It was also mentioned that consumers are unlikely to purchase fakes if they knew it funded terrorism. Most people outside the industry already find it implausible that purchasing fake items or illegally streaming content funds terrorism. Regardless of the validity of this scepticism, it heightens the burden of proof to be convincing. Having brand owners and brand protection vendors repackaged as global anti-terrorism organisations stretches credibility beyond plausibility.
“I polled people inside and outside the industry, asking ‘what punishment is fair for a person selling counterfeit Nike trainers?’ – unsurprisingly not one person said that 10 years was not long enough. Also, I asked ‘if the prison sentence was increased to 15 years do you think that would have dissuaded the brothers from committing that act of terrorism?’ – again no one agreed with that proposition.”
“I want to ask everyone here what they think about this. Can I have a show of hands, who here agrees that there is a link between counterfeiting and terrorism based solely on the last three slides I’ve presented regarding the Charlie Hebdo attack? Ok, a few hands going up, maybe, 30%-ish.”
“Funding for the attack was actually obtained primarily through a loan, which was fraudulently obtained. That was used to purchase the arms used during the attack. There were a number of other crimes involved, stealing cars for getaway vehicles for example. However, the money from counterfeiting was not a significant part of their income and was not connected with the terrorist attack. It was just one of many crimes the brothers were involved in living outside the legitimate economy. We need to be very careful when drawing some of these conclusions ‘they were involved in counterfeiting, they did conduct terrorism, therefore the two are intrinsically linked’. Let’s look carefully about what we report, a lot of this is sensationalism; this actually damages legitimate claims made by brand owners and links with other forms of criminality and illicit trade. The stats and anecdotal evidence is not as sound as it should be. The UNIFAB report is however definitely worth reading, I will come back to it in a few slides as it does make some interesting points outside the Charlie Hebdo example which are well-worth considering.”
a lot of this is sensationalism; this actually damages legitimate claims made by brand owners and links with other forms of criminality and illicit trade.
“We are now going to take a more ‘criminology’ perspective towards brand protection and the crime of counterfeiting. This is to look behind the crime, to understand why the crime happened, who is committing it, what forms of criminality are linked and how we can better reduce such crime in the future.”
Brand Protection Criminology

“Can anyone answer this question – which type of criminality was most frequently linked with IP crime in the UK?”
“Member of audience: money laundering”
“Great answer, money laundering is number two on the list, which I’m surprised it’s not number one, as we heard yesterday money laundering is concerned with the use of the proceeds of crime. Given there is already IP crime, I thought money laundering would be higher. “
“Any other guesses?……..I’ll give you a clue, it’s not terrorism…”
“Member of audience: identity theft”
Disclaimer – I did not hear this suggestion, it was made by a delegate towards the back of the room. I was informed about it during a break. It is a great guess, however, identity theft is not even on the list. Given the prevalence of brand piracy which facilitates phishing attacks, I am extremely surprised it is never on the list. To note, the links are as reported by law enforcement agencies and not based on actual criminal convictions, therefore the lack of identity theft or fraud being included is not due to the difficulties in prosecuting such offences or finding the perpetrator. Looking at the data, there is a greater representation of ‘offline’ offences being reported, which likely explains the anomaly within the results.
UK IP Crime ‘Links’
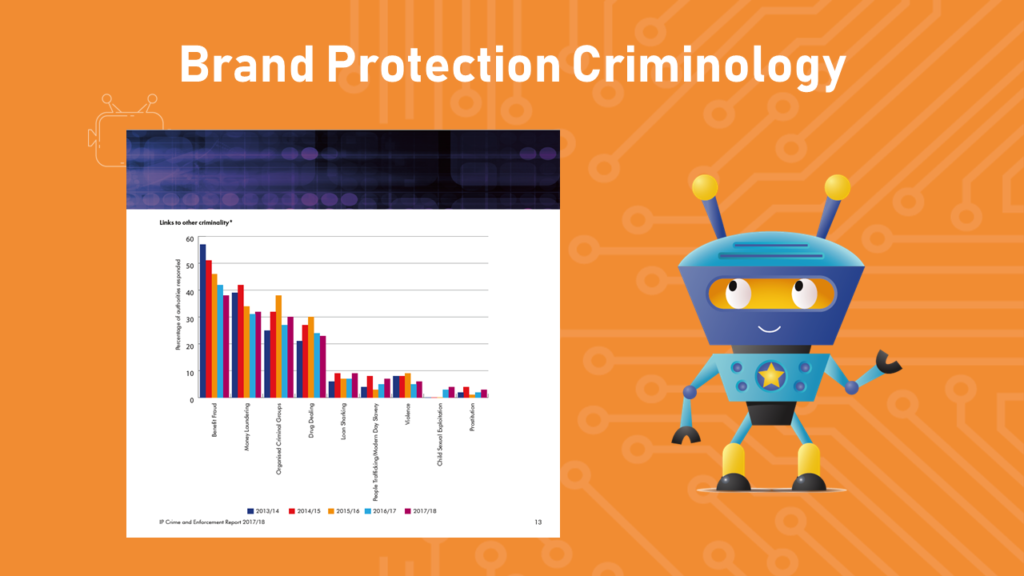
“Ok, if we have no more guesses here is a tiny chart that you probably can’t see so I will read it for you. These figures are taken from the 2018 UK IP Crime and Enforcement Report, the data shows the last five years, however, this information was not provided in the 2019 report which is why we are using the figures from 2018.”
“Number one – by far the biggest is ‘benefit fraud’. It is not terrorism, it is not organised crime or anything which normally makes the headlines. It’s benefit fraud.”
I was asked during lunchtime what was meant by benefit fraud. This refers to fraudulent social security claimants i.e. receiving money for unemployment when the person is employed or disability allowance by non-disabled persons. After explaining this, I was then asked how this could possibly link to intellectual property crime. There is no real link between the two. It is a quirk of the statistics relied upon. An infringer involved in IP crime and fraudulently claiming social security payments does not show the crimes are linked in any meaningful way, other than the offender is involved in various forms of criminality. They could both be categorised as a form of ‘economic crime’; a means of earning an income for those who operate outside the legitimate economy.
“Number two is ‘money laundering’, as we discussed. Number three is ‘organised criminal groups’, the third biggest area of criminality. Given the very broad definition we saw before, I’m again surprised the percentage reported isn’t a lot higher. Number four is ‘drug dealing’; when we talk about organised crime and drug dealing, naturally people’s mind wonders off to Colombia, to cartels, to Mexico [and Breaking Bad], but in this case we are not talking about that. We are talking about very low level, the last mile of drug delivery. I am not trying to down play this crime or the impact it has on communities, only saying it is not organised crime in the way you may think when linking it with drug dealing. We are talking about kids, teenagers on bikes in extremely deprived areas delivering drugs. There are gangs and organised crime within the supply-chain, however, what is being reported [is] not necessarily the major hardened criminals, but the very low level offenders who are generally easier to apprehend and convict.”
when we talk about organised crime and drug dealing, naturally people’s mind wonders off to Colombia, to cartels, to Mexico
In this context, drug dealing could also be looked at in terms of a common form of criminality the disenfranchised engage in- much like selling contraband and counterfeited goods and social security fraud.
“The next links are all relatively small, they are ‘loan sharking’, ‘people trafficking’, ‘violence’, ‘child sexual exploitation’ and ‘prostitution’. You might expect some of these to be more, such as trafficking, given the links with false labour, counterfeiting, illicit manufacturing and slavery. This report is from a UK perspective, in many other countries it is likely to be higher, but we barely manufacture anything legitimate let alone manufacturing counterfeits. That is probably why they are so low in terms of linked with IP crime.”
To note, the reported percentages are not actual volume in terms of number of criminal acts or offenders apprehended. The percentages actually represent the proportion of authorities which reported an offender for IP infringement alongside the identified ‘linked criminality’. This, combined with the lack of geographical mapping of the data prevents a more thorough analysis of the data.
Framing Global Counterfeiting

“Next, this is an excerpt from the Illicit Trade report produced by the OECD and the EUIPO in 2019. This report is definitely a must-read for the industry. It lists five areas that show propensity for a country in terms of selling, manufacturing or transporting counterfeit items. The first one is governance, the definition for the report was about the IP legal system and corruption in terms of enforcing that. Some countries may have what looks great on paper but they don’t enforce it due to corruption, customs officials taking bribes, that is what they mean by governance. Free Trade Zones explains itself.”
See the 2018 Out-of-Cycle Review of Notorious Markets report produced by the USTR for a discussion of Free Trade Zones in relation to IP infringement (listed below).
“Then, production facilities which was about labour, wages, trade unions and manufacturing regulations. Logistics capabilities is about transport networks and ports. And trade facilitation policies was specifically about transparency and sharing of data between countries, something which has been mentioned a number of times at this event. These five areas were identified in terms of global trade of counterfeit and pirated goods. I think this is a much better framing of the issue and how we go about putting some measures into place to reduce piracy.”
“Before we go on to another tiny chart that no one will be able to read, does anyone want to guess which country was identified as the biggest contributor to the global supply of counterfeit and pirated items? This is quite an easy one.”
“Member of audience: China”

“Yep, China. The top one is China, the second is Hong Kong (China). Over the past years of the OECD measuring China has always been the top, what I can say is that China as a proportion has been decreasing. Only modestly, but it has been going down. As you can see the issues are so big it will take a long time for them to climb the mountain and get to the other side. You can see no one else is even close. They (OECD) have another metric which is used and provides us with slightly better results.”

“Again, at the top is China and Hong Kong. They two should be consider as one category in itself. The prevalence of the issues is so big they need to be considered in isolation. There are two other categories, one is ‘transport countries’, so where the illicit goods are being routed through. For example, United Arab Emirates (third on the list) is a good example. There’s a bunch in there. The third category is countries with extremely weak labour regulations – low wages, poor factory conditions, we are talking about Pakistan, India, Cambodia. And more and more South-East Asia as production starts to move away from China as they improve labour conditions and IP governance. They offer even lower labour costs, be it Vietnam for example.”
“Member of audience: Vietnam isn’t on the list (an eagle-eyed front rower)”
“Yes the figures go up to 2016. It is a huge undertaking including qualitative data such as interviews with customs officials so the data is always behind. I would say a few countries in South-East Asia are likely to appear on the next report, this current report did also mention this trend towards the region, specifically mentioning Malaysia and others. I would predict Vietnam definitely being one of them as well.”
The regional differences are often not taken into account.
Turkey, along with a few other countries listed cross-over both categories stated, they are a manufacturer of IP infringing items and a country used as a transit point.
“Back to the UNIFAB report, almost all of the other instances of terrorism (asides from the Charlie Hebdo case discussed above) were in the Middle-East. Generally in war-torn countries which have suffered invasions and wars in recent years, areas where the is a power vacuum. What happens when there is a power vacuum – criminals and terrorists step in and takeover. We saw that with IS; they are listed in the UNIFAB report with a lot of activity being funded through counterfeiting. There were definitely links between the two (counterfeiting and terrorism) but it was restricted to certain regions of the world. And when we look at where most of the counterfeiting is occurring, its generally doesn’t match. The regional differences are often not taken into account.”
Global Counterfeiting Trends

“These are a few just different points from the OECD report I wanted to note. One of them is about the factors which increase propensity for counterfeiting also hep trade. For example, Free Trade Zones is an obvious one. FTZ benefit large corporations and rightsholders who utilise the zones. The second point is about small parcels; it has been increasing as a percentage of what has been found. Partly this is due to large containers routed through certain countries where there is corruption are not being caught in transit. What happens is then the items go into the small parcels delivery system where there is a higher chance of then getting caught (i.e. seized). I think that is what that reflects – that sometimes it is harder to get to the organised crime level due to corruption and we are often dealing with the very low-level [end of the supply-chain]. The final point is 58.5% of counterfeit and pirated products are sold to consumers who actually knew they were buying fake products. Which is a problem because demand fuels supply.”
The OECD report is usually serialised with the headline ‘as much as 3.3% of global trade is in counterfeit and pirated goods’. Whilst this does reflect the findings of the report the key information which aids with understanding global counterfeiting is then overlooked.
How To Reduced Structural IP Crime?
“How to reduce structural IP crime? From what we have just been speaking about, the first point is about demand. There was mention before about IP literacy, this is a hugely important point. Not in terms of teaching people the definition of copyright or a trade mark; generally I find from a lot of individuals, micro-SMEs for example, is that once they start creating something themselves, they understand the need for protection of their economic rights. Often, people don’t actually understand how IP protects their economic interests, teaching them that side, how they can use IP helps them understand and empathise with rightsholders. [Redacted]. The next one is about supply. Mostly they are being manufactured in Asia where there are huge problems with poor labour conditions. Many companies have great standards, but they don’t actively monitor compliance.”
Full Supply-Chain Transparency
We need to be able to go into a shop, buy a T-shirt, scan a QR code which can tell you where it is being imported from, where it was originally manufactured, which factory, is the factory compliant with applicable regulatory requirements. And, which person actually made it, are they getting paid a living wage, are they fired or beaten for joining a trade union, have they been trafficked. What we need is full supply-chain transparency.
“Actually, let me cover points two and three together. How is supply meeting demand. Both of these, what we need, is greater transparency. We need full transparency from consumer to manufacturer. This includes the person actually sowing the T-shirt together. We need to be able to go into a shop, buy a T-shirt, scan a QR code which can tell you where it is being imported from, where it was originally manufactured, which factory, is the factory compliant with applicable regulatory requirements. And, which person actually made it, are they getting paid a living wage, are they fired or beaten for joining a trade union, have they been trafficked. What we need is full supply-chain transparency. Once we have this, it will really reduce the spaces criminals have to operate within. Right now criminals have lots of space, they are breathing easy, they are having fun. It is far too easy to get away from this because we don’t know where anything comes from. That is the biggest thing we can do – full transparency in the supply-chain. Just as corporate social responsibility and then sustainability became vital to corporations and brands, full supply-chain transparency will. It needs to be everywhere.”
Supply-chain management is intrinsically linked with sustainability. A point mentioned numerous times in recent years is the environmental harm counterfeiters cause through a lack of compliance with environmental regulations.
Operating outside the legitimate supply-chain provides significant advantages for criminals, including not complying with environmental standards, or health and safety. Electrical goods are a common example reported on, with items presenting a significant fire risk. Foodstuffs is another area poor manufacturing standards presents an obvious risk, along with many other categories.
Book Promotion

“This is my final side (proceeds to deliver sales pitch for his book) – Digital Brand Protection: Investigating Brand Piracy & Intellectual Property Abuse. This is my book available on Amazon, which discusses many of the things we have been discussing over the past day and a half. For example, the different types of pirate websites, discussion of big platforms which are used for counterfeiting and piracy. There was some confusion yesterday about a trend of “Instagram to Taobao” – Instagram is banned in China; Taobao only sells domestically in China, so whoever is using that business model won’t be making a lot of money from it. The book helps those who see this and misunderstand the culture and workings of the platforms. The book is only focused on the digital side (for now), so if anyone has any digital counterfeiting or piracy issues and wants to learn about how to investigate that online, then this book is of use to you. Thank you.”
References
https://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=CELEX:32001L0029:EN:HTML
https://www.gov.uk/government/publications/annual-ip-crime-and-enforcement-report-2018-to-2019
https://www.gov.uk/government/publications/annual-ip-crime-and-enforcement-report-2017-to-2018
https://www.oecd.org/gov/risk/trends-in-trade-in-counterfeit-and-pirated-goods-g2g9f533-en.htm
https://www.unifab.com/en/counterfeiting-terrorism/




[…] authorities, or even to know their identity in the first place. The result is an endless game of “whack-a-mole”: illegal content is taken down, but immediately reappears elsewhere. This status quo enables […]