How To Conduct A Strategic Review
Brands are one of the most powerful and long-lasting ways of creating value for a company. The internet enables all businesses to access a wider market than ever before, directly connect with customers and build brands with purpose. Social networks, smartphones, cyber-libertinism, the growth of digital entrepreneurship, the explosion of E-Sports and the constantly connected lifestyle have led to an irreversible transformation in how consumers engage with a brand. The direct-to-consumer channel is rapidly evolving; individuals are becoming brands, including content creators, influencers and key opinion leaders; and even ‘causes’ have become branded.

Opportunity brings risk. A consequence of a successful brand is infringement. Success breeds imitation and attracts scammers. With digitisation has come greater exposure to piracy, online harms, cyber-risks, dilution, reputational damage, financial risks and intellectual property infringement. Media previously inseparable from physical artefacts enabling consumption can now be freely distributed across the internet in an instant. Brands must guard their assets from tarnishment and prevent the dilution of consumer touchpoints. This, is the concept of brand protection.
Brand protection is a mindset, not a narrow discipline; an approach which emboldens brands and creativity. A strategic review must consider the bigger picture encapsulating all elements of brand IP, brand building and digital culture.
A complete assessment of scope must be conducted internally. This must interface with various internal functions including: legal; logistics; marketing; security; brand management; and finance. If brand protection activities are conducted without working alongside other internal functions, it is not a strategy, just a collection of ad hoc measures. Simply hiring an expert or contracting with a solution provider is not a strategy, it can form part of a strategy, but should never be used to justify weak internal participation in brand protection activities. Internal and external capabilities must be regularly benchmarked with efficiency and long-term effectiveness at the forefront of the process. Such a review can be broadly broken down into four stages: scope; plan; execute; and evolve.
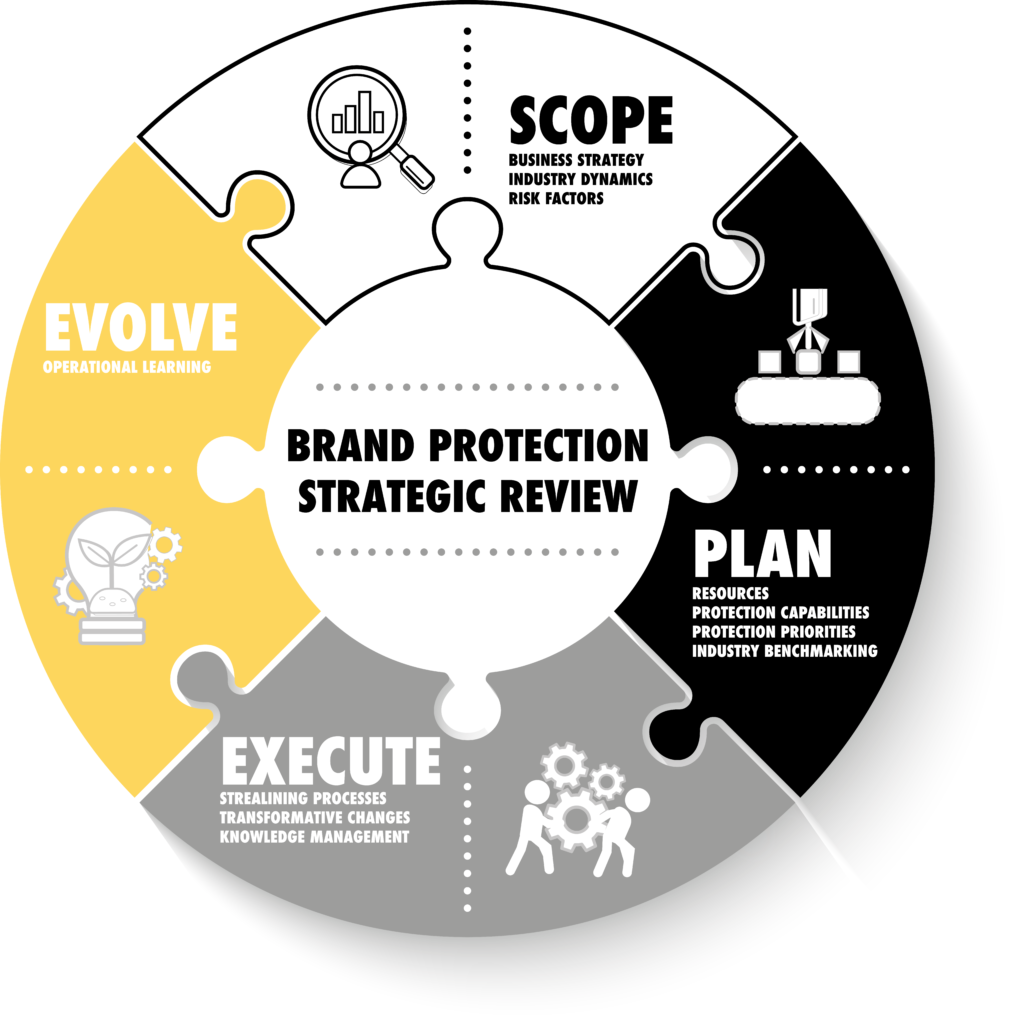
1 – Scope
This stage is fundamental to align all brand protection activities (and budget-spend) with the business strategy, and to understand market conditions and risk-factors. The scope of the core business determines the remediation paths, necessity for technological solutions and risk exposure of the brand.
Business strategy – strategic objectives should drive all brand decisions, in particular, objectives to enhance customer experiences should be priority. A brand is intrinsically linked to trust. Therefore, activities which abuse brand assets to defraud customers must be of the highest priority. For example, outbound phishing attacks exploiting a brand owner’s trade marks erode customer trust. A website claiming affiliation but with no traffic may be deemed a relatively low priority, whereas a website which defrauds users of personal information or for financial gain represents a greater customer experience risk.
Industry dynamics – key industry changes must be considered to ensure the brand protection strategy is forward-looking, developed with preparedness to facilitate agile responses. Industry dynamics include general economic conditions, technological changes, and regulatory environment.
Risk factors – brand risks are those which adversely impact brand assets or customer experiences. By enforcing IPRs, a rightsholder precludes negative customer experiences caused by infringers appropriating brand assets. Risk factors must be considered broadly, to include valuable brand assets and IPRs, but going beyond to also encompass customer data, know-how and security risks. Brand protection must connect traditional activities with cyber-security, anti-fraud, and compliance monitoring of both authorised and unauthorised uses of assets within distribution channels.
2 – Plan
This stage provides the analysis to the strategic alignment, becoming the integral link in the bi-directional flow of data through strategy to implementation. The analysis must be data-driven, focusing on availability of resources, protection capabilities and priorities, and employ industry benchmarking for accountability.
Resources – a review of strategic approach and risk appetite must be considered in light of available resources. This includes the structure of the team responsible for core brand protection activities and interactions with other relevant areas (i.e. cybersecurity). Analysing resources is straightforward, following a checklist in an audit style process to identify all relevant information.
Protection capabilities – assessing internal and external capabilities to handle the range of issues causing harm to brand assets and customer experiences. Capabilities analysis must first assess the aggregate brand protection capabilities, and then the disaggregate, to apportion capabilities by availability from internal resource or provided by external service providers.
Dividing the analysis in this manner identifies inefficiencies within specific areas, facilitating the testing of incremental changes. Rightsholder often find they are paying multiple vendors for services with significant overlap and little value add.
Understanding capabilities in the aggregate is to measure effectiveness, alignment with strategy, interoperability of systems, inefficiencies caused by overlap or lack of interoperability, breath and depth of coverage, and adaptability to predicted or unforeseen future risks.
Internal capability analysis focuses on structures, resiliency, identifies gaps necessitating external services and if externally provided services would benefit from in-housing. External capability analysis focuses on coverage of services provided by suppliers extending to brand protection, digital risk protection, ad monitoring, compliance monitoring, sentiment analysis etc.
Measuring the cost-efficiency of external providers is vital to ensure the most effective means of monitoring and remediation is taken. Also, understanding the vision of external providers mitigates against a lack of preparedness for future threats.
Protection priorities – the level of resource available and current capabilities shapes the setting of priorities. However, limiting priorities under these constraints removes the necessarily forward-looking aspect in strategy. Priorities must therefore flow from a strategy which aligns with commercial objectives. Using the protection of brand assets and customer experiences as the guiding light ensures a strategic outlook. High priority threats may come from the intersection between brand protection and cybersecurity or from speedily removing infringing streams of a live broadcast – priorities depend on the nature of the rightsholder and assets being protected. Setting priorities is always a consultative process, drawing on data and insights from all relevant stakeholders including, senior management, legal, security, marketing and external providers.
Industry benchmarking – resources, capabilities and priorities must be benchmarked against industry competitors. Drawing on data from all available sources and proprietary methodologies, benchmarking measures the effectiveness of existing activities and future activities. Metrics used must encompass the entire extent of the protection program. This will go beyond measuring number of threats or threats remediated to include the impact of such threats through monitoring of negative customer experiences and dilution of assets. Benchmarking provides accountability and generates data as part of the bi-directional flow of data through strategy to implementation.
3 – Execute
This stage implements the plan agreed upon by all relevant stakeholders after conducting the strategic review and data-driven analysis. Execution requires an actionable plan plus internal buy-in; therefore, an appropriate level of internal communication and training is required to ensure new policies are adopted without disruption.
Streamlining processes – changes targeting inefficiencies identified during the analysis phase (including stakeholder input and strategic review) must be incrementally streamlined. A connected approach to protecting brand assets and customer experiences requires continual incremental changes to reduce inefficiencies, each being measured independently. Measuring the effect of changes during the implementation phase ensures priorities are managed according to their maximum overall impact. Narrow ROI calculations which only serve as vendor propaganda must be avoided at all costs. Robust policies must be formalised around best practices to ensure effective work streams are in place and reduce interface points of friction.
Transformative changes – more fundamentally transformative changes identified during the analysis phase (including stakeholder input and strategic review) must have a business case developed. Such changes can be more difficult to measure compared to incremental changes. A longer-term view of performance must be taken to allow space for the newly implement measures to transcend through the organisation, instilling brand protection thinking across departments. Detailed KPIs are required for all recommended changes to ensure transparency and accountability. Areas which typically fall into the transformative category include adjustments to risk appetite, digitisation, technological future-proofing, introducing automation into work streams, stakeholder management, supplier management and engaging with new customer touchpoints.
Knowledge management – a system dedicated to brand protection knowledge management is often under-valued. Knowledge management assists with internal communications and training, which in turn leads to stronger buy-in from relevant stakeholders. Using a knowledge management approach develops the ‘brand protection thinking’ desired. Combining knowledge generated through the analysis process, strategic review and ongoing monitoring of iterative changes with proprietary methodologies will create a best in class strategy. The strategy will encourage stakeholder engagement and collaboration across relevant departments.
4 – Evolve
Any brand protection strategy must be agile, learning iteratively to streamline processes and continually reduce inefficiencies. Utilising operational learning develops an adaptable strategy fit for the hyper-fast digital economy.
Operational learning – this step connects the entire process, transforming it from being a discrete process into a long-term mechanism for driving excellence and efficiency. As a process, operational learning is about asking important questions which overtime identify trends and learning outcomes. Consistently driving operational efficiency indirectly impacts brand value, by reducing costs and improving outcomes. The process should ask questions such as:
Can the brand protection strategy be considered a success? What lead to the success? Which changes had the maximum overall impact? Which changes did not go well? What challenges were faced? Could the challenges have been better predicted? What unforeseen risks are emerging which require a response? How quickly can the organisation respond?
For more on developing a strategy with brand value as the guiding light:
For more on brand protection strategy & investigations, check out the book: Digital Brand Protection